It’s an unsettling scenario for WordPress administrators. A new phishing campaign has been discovered that specifically targets WordPress websites. The phishing email is craftily designed to appear as if it’s from the WordPress team, warning users of a “Remote Code Execution [RCE]” vulnerability identified as CVE-2024-46188 or CVE-2023-45124.
The aim? To trick users into infecting their sites with a malicious plugin. This deceptive strategy was uncovered and reported by security experts at Reliqus Consulting.
If you have also received such an email and think your website has been compromised, contact us now for a complete security audit and malware removal.
REQUEST WORDPRESS WEBSITE MALWARE REMOVAL NOW
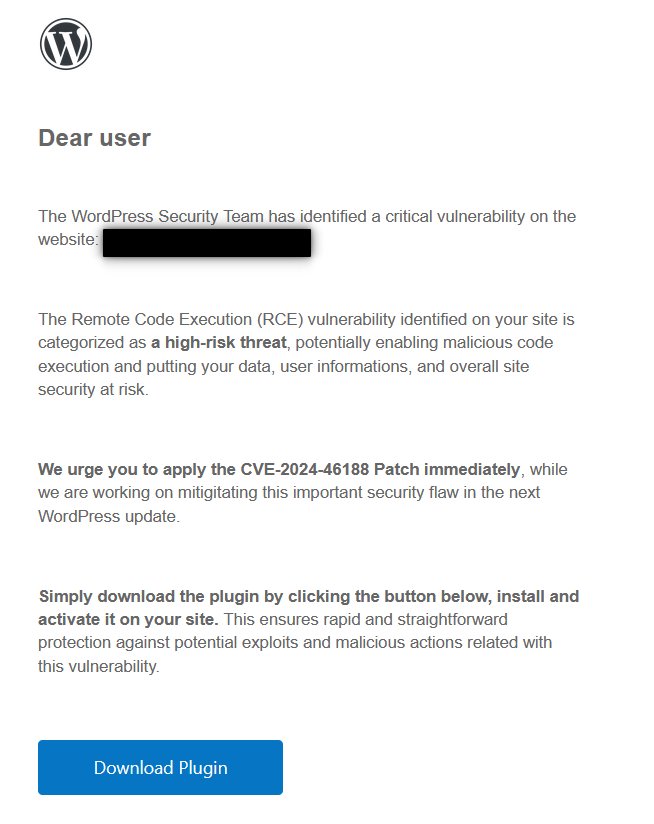
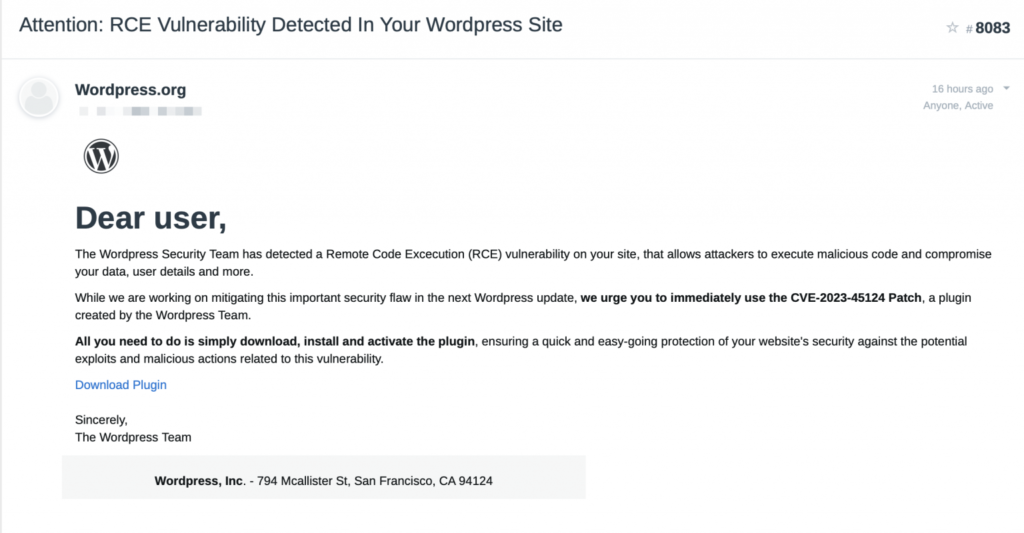
The email urges users to download a supposedly official plugin to fix the CVE vulnerability. However, do not download or install this plugin!
This plugin is infected with malware, and if installed, will infect your website with a backdoor and create a malicious administrator account.
As long as you do not download and install the malicious plugin, this campaign won’t affect your site. Remember, WordPress never asks you to install a patch to address a vulnerability. Instead, they would release a new version of WordPress core as a security update.
WordPress also advises:

Overview of the Phishing Page
Once the victims clicks the “download plugin” button from the phishing email, they are led to a site that is a near-perfect clone of the authentic WordPress.org site. These fraudulent sites, masked under domain names like wordpress[.]secureplatform[.]org and en-gb-wordpress[.]org, are alarmingly realistic.
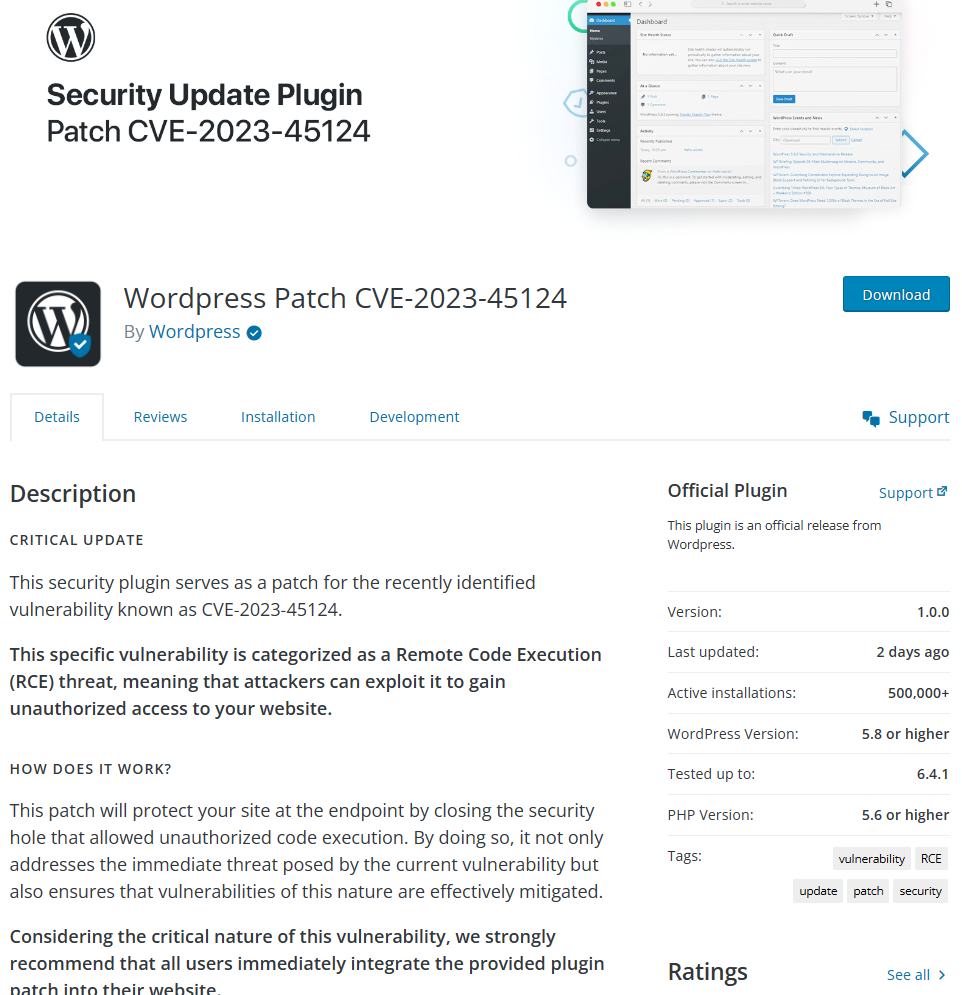
The scammers have gone to great lengths to make the phishing page appear legitimate. They have posted fake reviews on the page, singing praises of the fraudulent plugin.
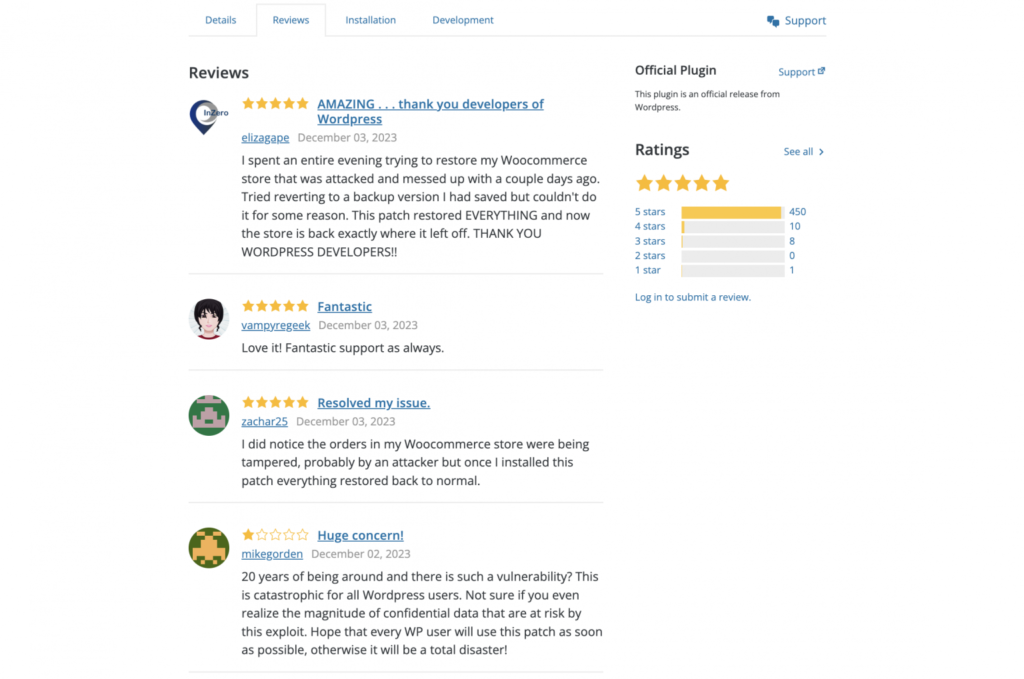
But, the deceit doesn’t end there. The fraudsters have targeted prominent figures from the WordPress ecosystem, listing them as authors of the malicious plugin.
This list includes well-known core contributors, Automattic employees, and individuals from leading WordPress agencies like 10up and MindSize. The attackers’ intent is clear: to give their scam an air of legitimacy and trick unsuspecting WordPress administrators.

Technical Breakdown of the CVE Phishing Campaign Malware
Upon receiving the phishing email, users are prompted to download a plugin with a filename such as CVE-2024-46188.zip or CVE-2023-45124.zip. This filename varies based on the domain used for the fake CVE phishing campaign, and multiple file names may exist.
Once the plugin is installed and activated, a message displays stating, “CVE-2023-45124 has been patched successfully”. The hackers encourage sharing the fraudulent patch, aiming to infect as many WordPress websites as possible.

What actually happens is the following:
- Upon installing the fraudulent plugin, the phishing campaign malware initiates its attack by generating a random password for a new username, ‘wpsecuritypatch’, with administrator privileges.
- A HTTP GET request is sent to their server, specifically targeting wpgate[.]zip/wpapi. This request includes a ‘siteurl’ query parameter loaded with base64 encoded data, representing the URL of the victimized WordPress site and the new administrator account’s password.
- Next, a HTTP GET request is sent to wpgate[.]zip/runscan. This returns additional base64 encoded data, which is then decoded and stored in a wp-autoload.php file in the WordPress site’s root folder.
- Astoundingly, the malicious plugin cleverly hides itself from the plugin list, along with the rogue admin account.
Take a peek at the screenshot below to see a fragment of the malicious plugin’s code. “Ironically, the comments written by the malicious user directly tell you what the malicious code under it is doing” – source unknown. This is just a glimpse of the intricacy of the WordPress phishing scam operation.

The presence of the wp-autoload.php is a potent backdoor, capable of injecting advertisements, redirecting users, launching DDoS attacks, swiping billing information, and even blackmail.
User Experiences and Threat Messages
In our investigation, we came across several instances where WordPress users received threatening messages attempting to lure them into the phishing scam.
Below are some screenshots and excerpts:
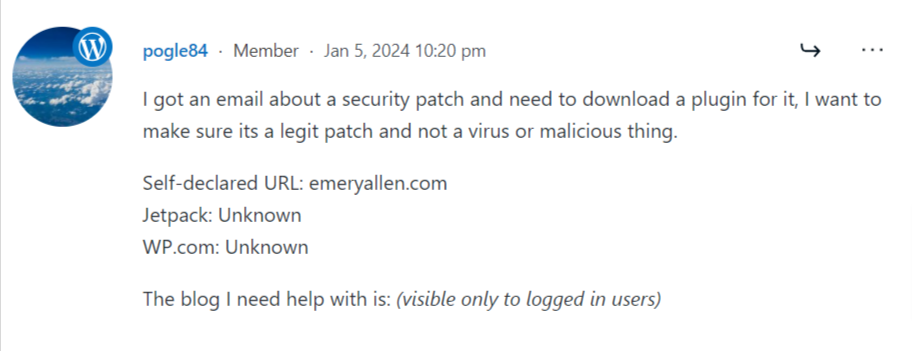
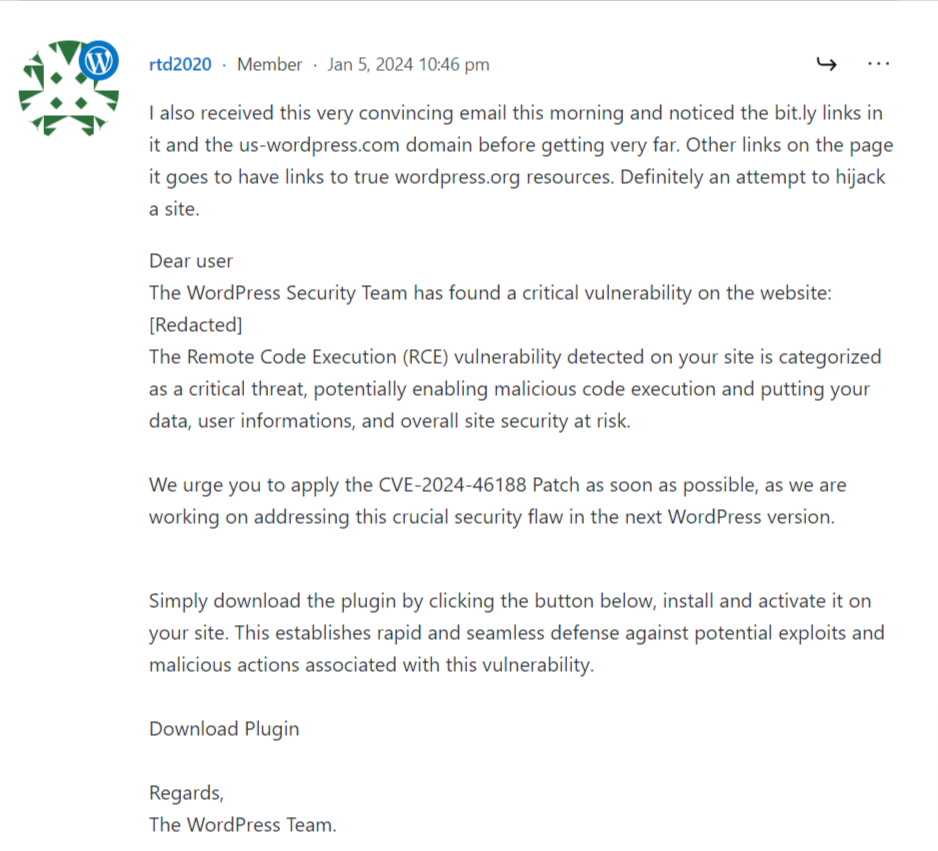

Notably, these phishing emails weren’t limited to a handful of users. Quite alarmingly, a large number of WordPress users reported receiving such emails.
Indicators of Compromise [IOCs]:
If your WordPress site has fallen prey to this CVE phishing scam, there are a few clear signs to look out for.
- A hidden user with the username wpsecuritypatch may have been created.
- You might find a suspicious file called wp-autoload.php in your WordPress root folder with a SHA-256 hash of ffd5b0344123a984d27c4aa624215fa6452c3849522803b2bc3a6ee0bcb23809.
- A new folder, either named wpress-security-wordpress, CVE-2024-46188 or cve-2023-45124 exists in your /wp-content/plugins/ folder.
- Additionally, check for outgoing requests to wpgate[.]zip.
- Watch out for malicious domains like en-gb-wordpress[.]org or -defcve[.]com, or emails from no-reply[@]mailing-wordpress.com.
- Be cautious of URLs like:
– https: //us.en-wordpress[.]org/plugins/cve-2024-46188/
– https: //defcve[.]com/runsccan
– https: //defcve[.]com/wpapi?siteurl=
Please note that these variables might change in the future as attackers adapt their tactics.
Protecting Yourself and Your WordPress Site from the Scam
Safeguarding your WordPress site from this scam involves vigilance and proactive measures.
- Always verify the authenticity of such emails; remember that WordPress usually communicates through your site’s dashboard, not via email.
If you ever encounter suspicious activity, knowing how to handle it is essential. Check out our guide on How To Remove Malware From Your WordPress Site? for step-by-step instructions on dealing with potential security threats.
- Avoid clicking on unknown links or installing unexpected software. Remember, haste makes waste. A cybersecurity threat may prompt you to act quickly, but it’s more important to act wisely.
- Moreover, regular updates to your WordPress site and plugins are crucial. Always ensure you’re downloading updates from official sources. Consider using security plugins for an added layer of protection.
Adopting these measures will protect your site against the fake CVE phishing scam and a whole host of threats targeting WordPress websites.
What to do if your WordPress Website has been Infected with Malware?
If you fear your WordPress site has fallen victim to the CVE phishing scam, act swiftly! Start by changing all passwords and reviewing user roles, specifically any suspicious ones like wpsecuritypatch.
Next, conduct a thorough scan for unauthorized plugins or users. Your site’s safety is paramount, so don’t hesitate to reach out to the expert WordPress security team at Reliqus Consulting for help. We specialize in WordPress malware removal services and can swiftly address your website’s security concerns.
Whether you’re dealing with the aftermath of this scam or have general security concerns, our team is equipped to handle it all. With our extensive experience in addressing complex cybersecurity challenges, you’re in safe hands.
Remember, it’s crucial to remain vigilant. We’re just a call away if you have questions or need assistance battling the CVE phishing campaign. For those who have already fallen for the scam, don’t despair. We’re here to help you navigate this issue and restore your website’s security.
Let’s tackle these cybersecurity challenges together and continue making the web safer.

